Fabulous Tips About How To Prevent Xss Attacks
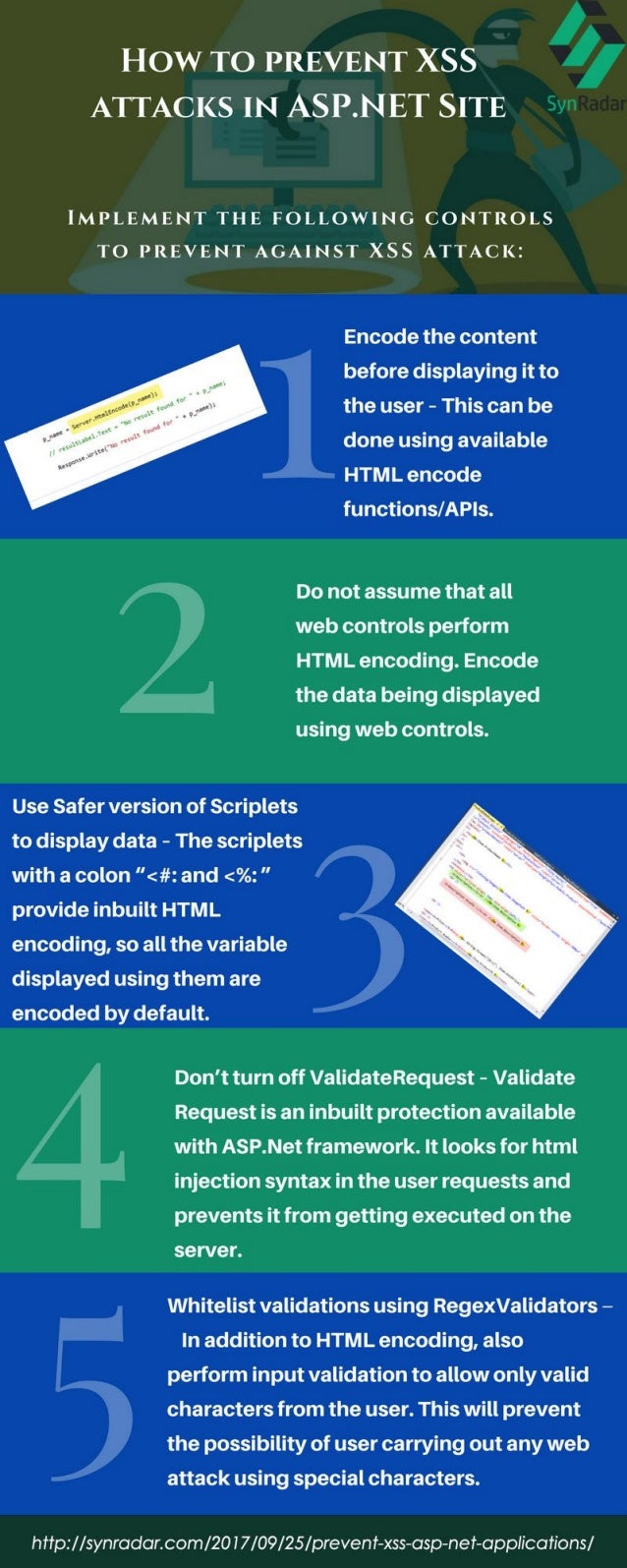
Filter your inputs with a whitelist of allowed characters and use type hints or type casting.
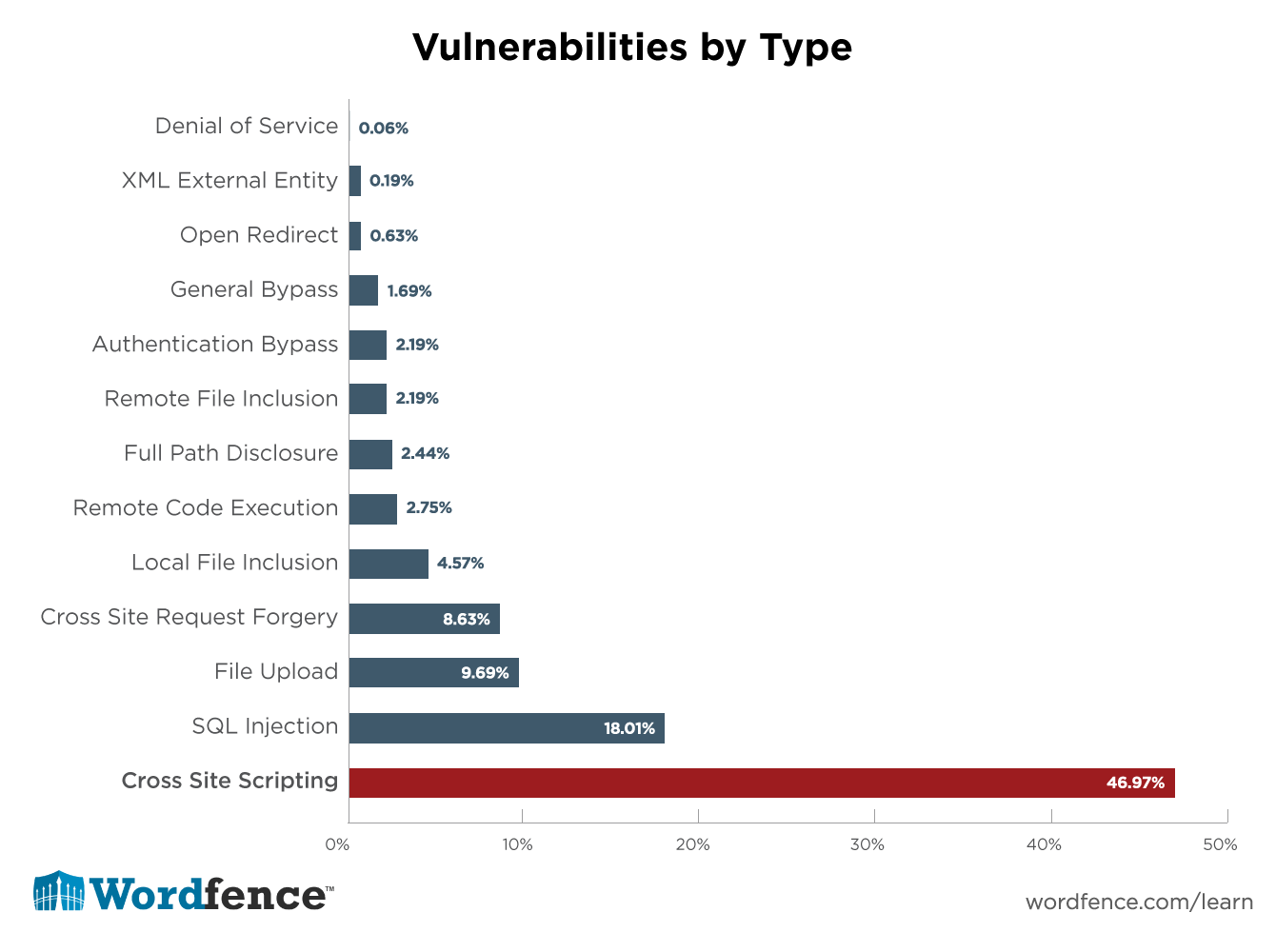
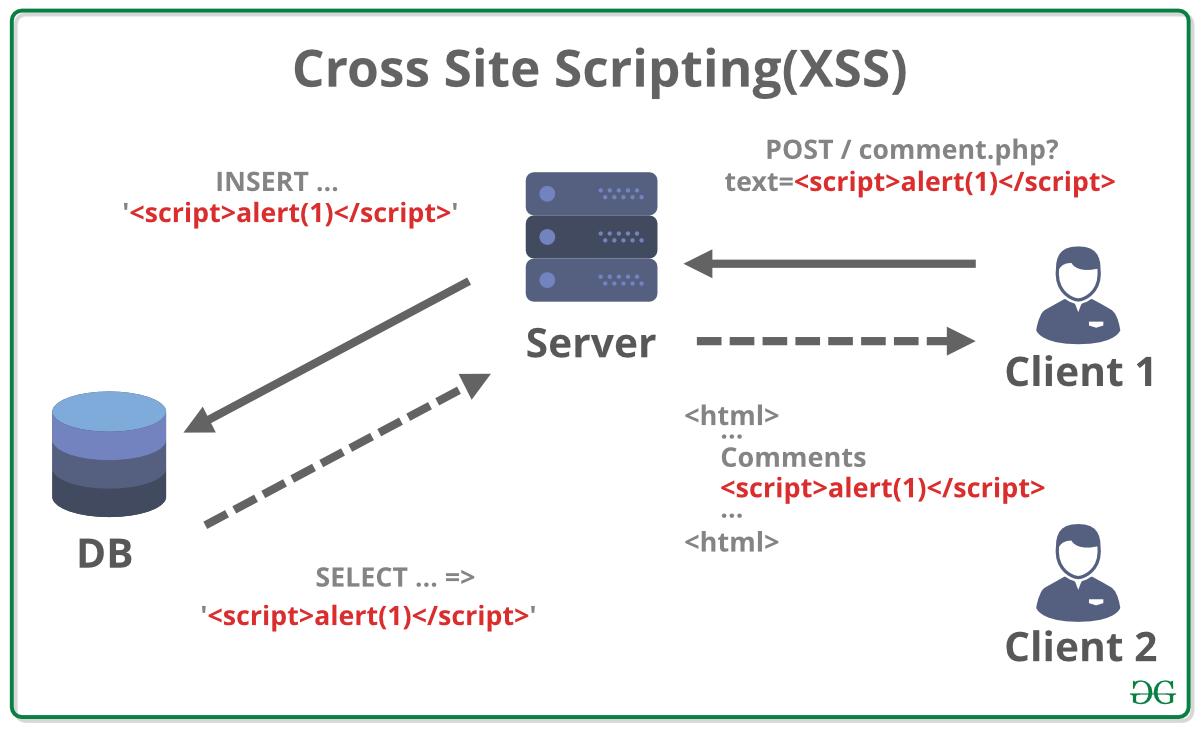
How to prevent xss attacks. Validation means checking that the input conforms to the expected format and. How to prevent xss. Types of cross site scripting attacks.
The owasp esapi project has produced a set of reusable security components in several languages, including validation and escaping routines to prevent parameter tampering. I've seen numerous other posts on this topic, but i have not found an article that clear and. Stop ransomware rmm attacks today.
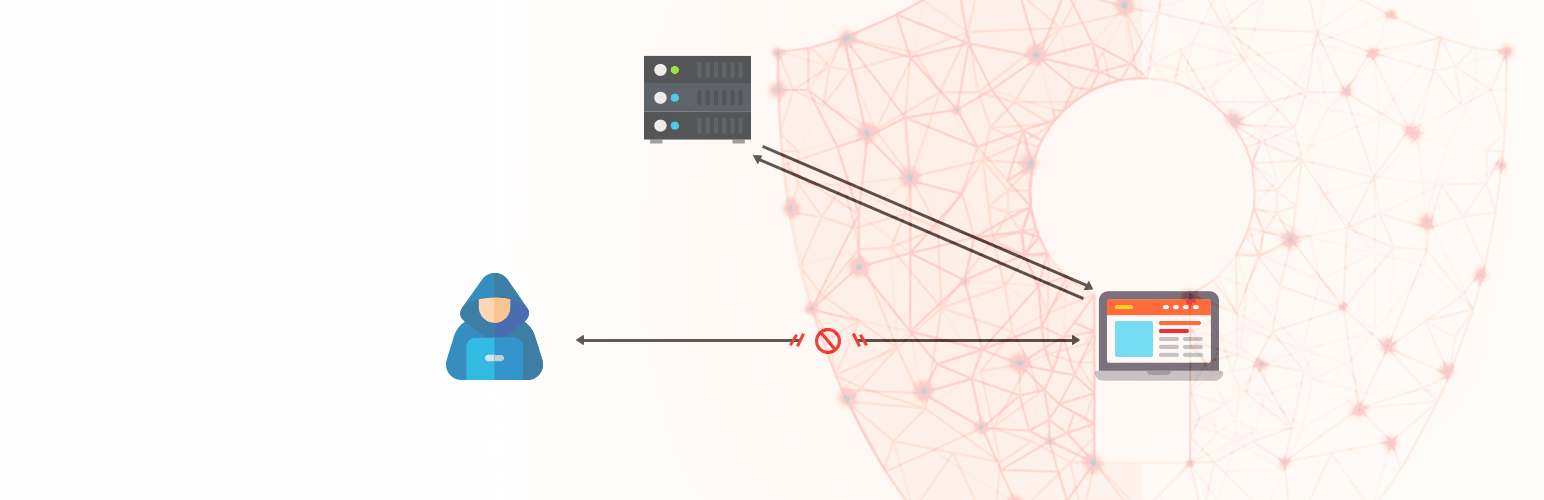
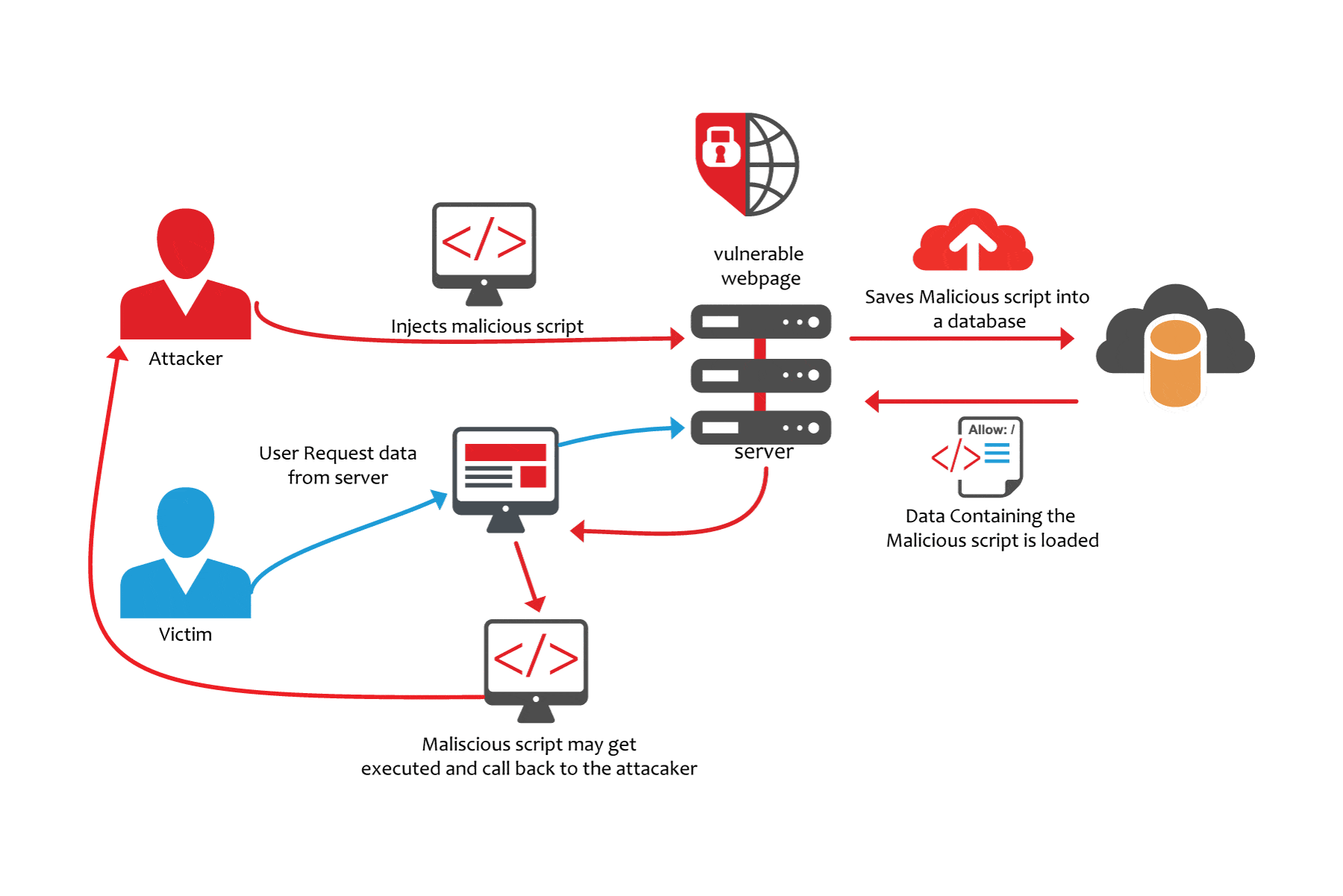
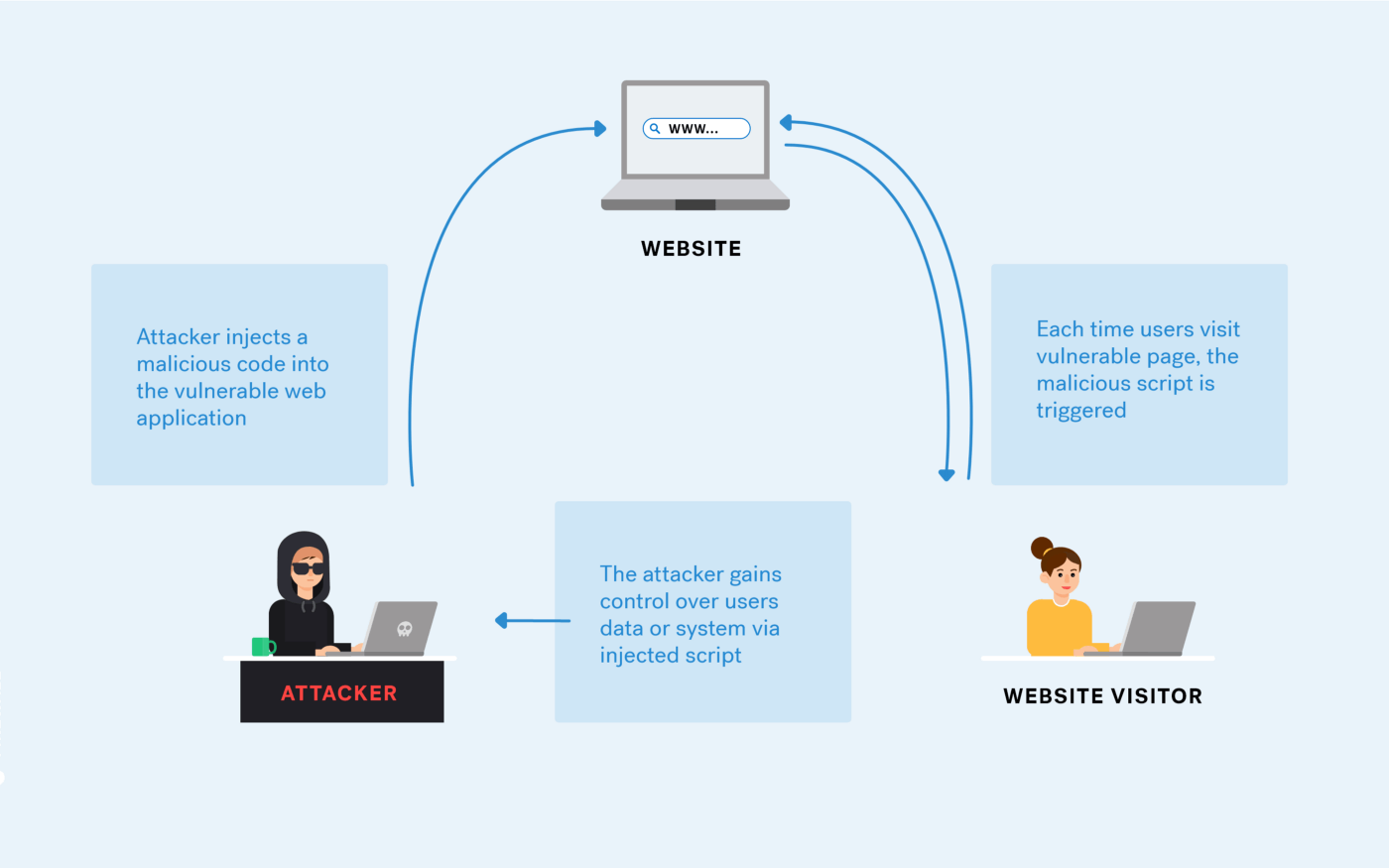
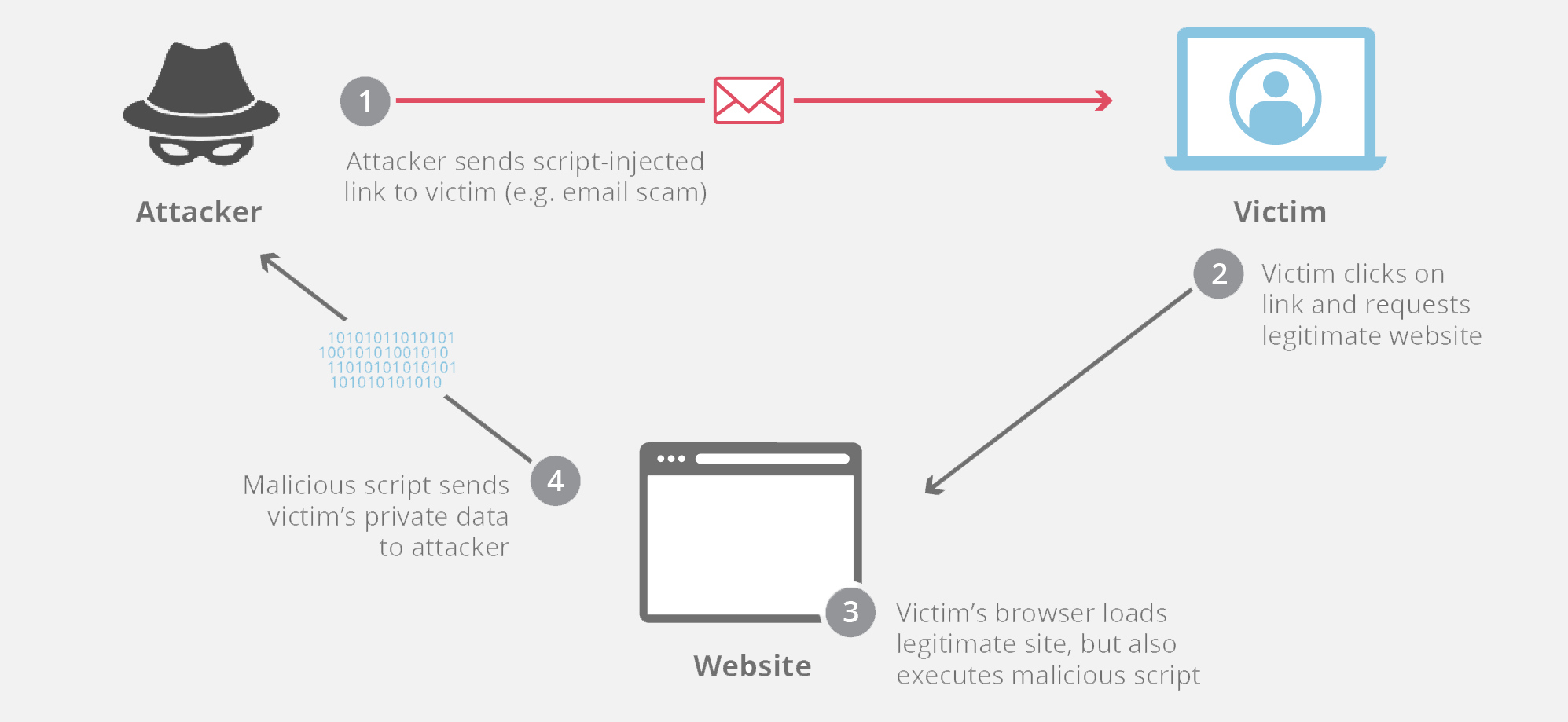
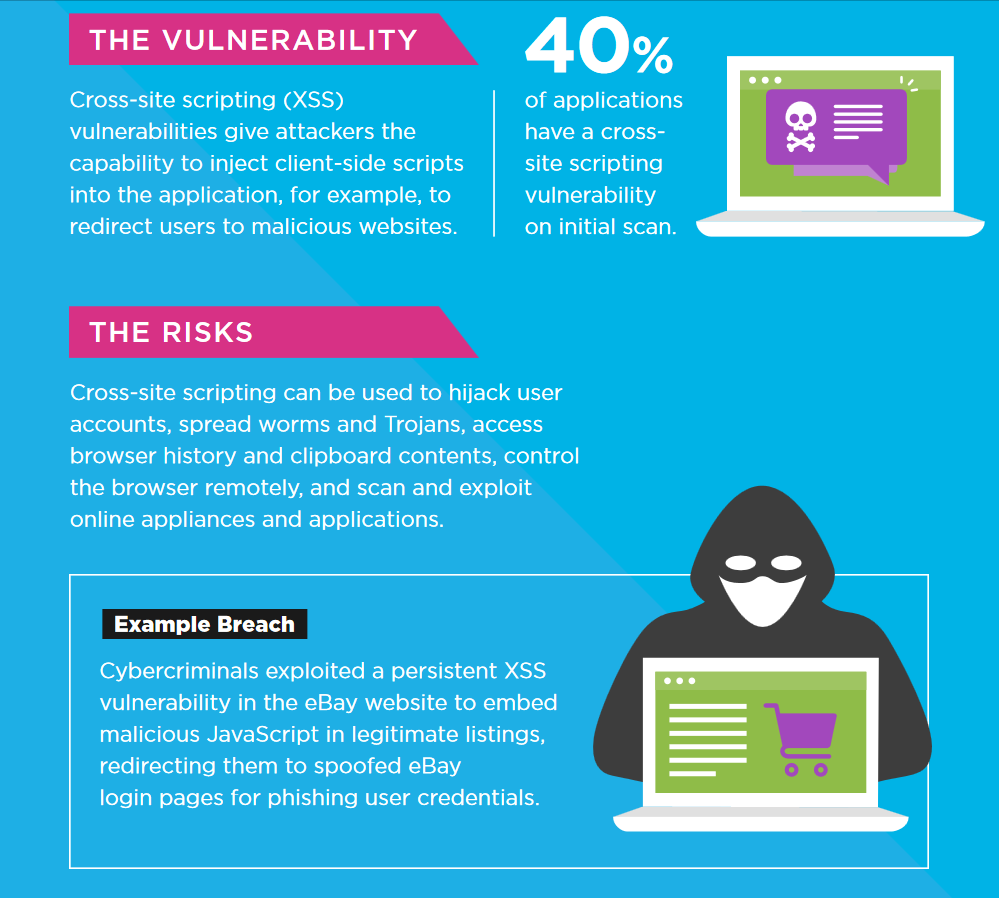
Xss enables an attacker to execute malicious scripts in another user's. One of the best ways to prevent xss attacks is to perform an audit of all user inputs in your app to determine what makes its way to html output without being. Although xss attacks can be serious, preventing the vulnerabilities that enable them is relatively easy.
How to prevent xss in your web applications. Escape your outputs with htmlentities and ent_quotes for html contexts, or javascript unicode escapes for javascript contexts. To prevent xss attacks, web apis should implement input validation and output encoding.
So, let’s take a looking at the definition of xss. Get started free. The best way to prevent xss is to validate and sanitize all user input and output.
Organizations need to include xss detection and prevention as part of their overall cybersecurity strategy to protect their website visitors and reduce the risk of. How to test against xss? Here we’ll look at how xss attacks work;
To prevent xss attacks, developers must validate user input by properly filtering out or escaping special characters and then encoding the output to prevent. How do i prevent xss in php? Since no single technique will solve xss, using the right combination of defensive techniques will be necessary to prevent xss.
Preventing xss attacks through filtering and sanitation. Marc dahan specialist in online privacy. This typically happens on dynamic web.
Fortiguard labs threat intelligence. How is xss being performed? Important coding, prevention and security steps;
Input validation ensures that user input meets expected criteria and.
![How to prevent Cross Site Scripting(XSS) attack in your Website? [EASY TIPS 2020] Red Server Host](https://blog.redserverhost.com/wp-content/uploads/2020/05/HOW-TO-PREVENT-CROSS-SITE-SCRIPTING-copy.jpg)